Create Cloud Identity on Azure¶
This guide will walk you through creating a managed identity on Azure and grant it permissions to access your Azure storage account. Rok will assume this identity to access your storage acount.
See also
- Azure Pod Identities on Official Azure Docs.
Overview
What You’ll Need¶
- A configured management environment.
- Your clone of the Arrikto GitOps repository.
- An existing AKS cluster.
- Permissions to create managed identities.
- An Azure Storage Account.
Procedure¶
Switch to your management environment and retrieve the name of your storage account, as you are going to use it in the following steps:
root@rok-tools:~# echo ${STORAGE_ACCOUNT_NAME?} roka8eb022arriktoarriktoSelect the namespace in which to deploy Rok:
root@rok-tools:/# export ROK_CLUSTER_NAMESPACE=rokSelect the name of the Rok cluster:
root@rok-tools:/# export ROK_CLUSTER_NAME=rokSelect the name of the managed identity Rok will use to access your storage account:
root@rok-tools:~# export AZ_MANAGED_IDENTITY=rok-${AKS_CLUSTER?}-${ROK_CLUSTER_NAMESPACE?}-${ROK_CLUSTER_NAME?}Remove the Rok cluster namespace and name from the managed identity name if they are both equal to
rok:root@rok-tools:~# export AZ_MANAGED_IDENTITY=${AZ_MANAGED_IDENTITY%-rok-rok}Create the managed identity and grant it the necessary permissions. Choose one of the following options, based on how you are managing your Azure resources.
Obtain your managed identity name and copy it to your clipboard, as you are going to use this value in later steps:
root@rok-tools:~# echo ${AZ_MANAGED_IDENTITY?} rok-arrikto-clusterGo to the Managed Identities service in Azure Portal.
Click Create.
On the Basics page, set the following options:
Set Resource group to arrikto so it matches the resource group of your AKS cluster.
Set Region to East US so it matches the region of your AKS cluster.
Set Name to the managed identity name you created above.
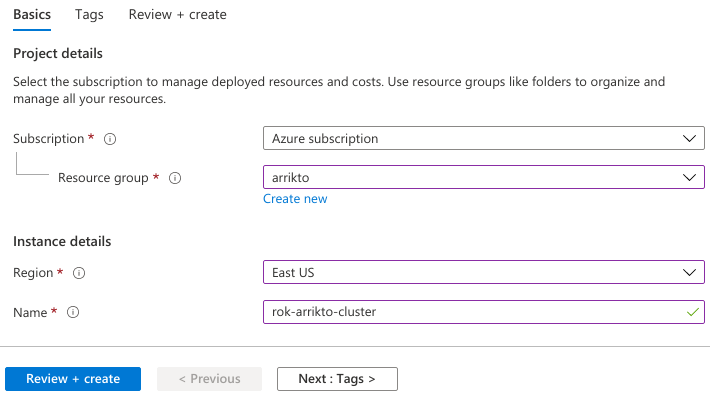
Click Review + create.
Click Create.
Wait for the deployment to complete, and click Go to resource to view the managed identity you created.
Click on the Azure role assignments tab.
Click Add role assignment.
Set the following options:
- Set Scope to Storage.
- Set Subscription to your desired subscription.
- Set Resource to the name of the Storage Account you created for Rok.
- Set Role to Storage Blob Data Contributor.
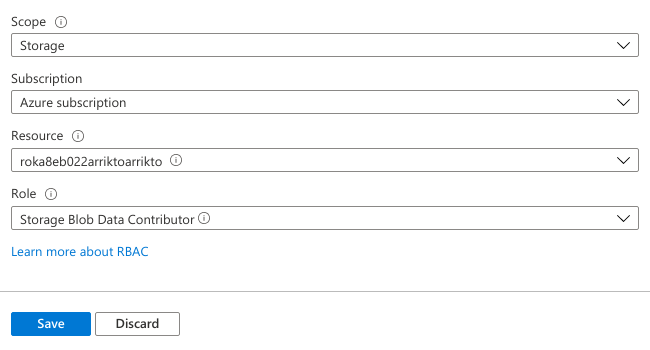
Click Save.
Create the managed identity:
root@rok-tools:~# az identity create \ > --name ${AZ_MANAGED_IDENTITY?} \ > --resource-group ${AZ_RESOURCE_GROUP?} \ > --location ${AZURE_DEFAULTS_LOCATION?} { "clientId": "8801729b-2217-446f-8542-829e49bf90e9", "clientSecretUrl": "https://control-eastus.identity.azure.net/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourcegroups/arrikto/providers/Microsoft.ManagedIdentity/userAssignedIdentities/rok-arrikto-cluster/credentials?tid=2bf793e0-71b3-4a6c-ba8a-96a6755de088&oid=87959b52-1687-4a8f-858a-2dcbeda4c22a&aid=8801729b-2217-446f-8542-829e49bf90e9", "id": "/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourcegroups/arrikto/providers/Microsoft.ManagedIdentity/userAssignedIdentities/rok-arrikto-cluster", "location": "eastus", "name": "rok-arrikto-cluster", "principalId": "87959b52-1687-4a8f-858a-2dcbeda4c22a", "resourceGroup": "arrikto", "tags": {}, "tenantId": "2bf793e0-71b3-4a6c-ba8a-96a6755de088", "type": "Microsoft.ManagedIdentity/userAssignedIdentities" }Troubleshooting
The command failed with an authorization error
If the above command fails with an error message similar to the following:
The client '0c799e27-a84f-41a2-a02b-236af002af99' with object id '0c799e27-a84f-41a2-a02b-236af002af99' does not have authorization to perform action 'Microsoft.ManagedIdentity/userAssignedIdentities/write' over scope '/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.ManagedIdentity/userAssignedIdentities/rok-arrikto-cluster' or the scope is invalid. If access was recently granted, please refresh your credentials.it means that your identity does not have sufficient permissions to create a managed identity.
To proceed, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has
Ownerpermissions. If you only haveReaderpermissions, contact your administrator to grantOwnerpermissions to your identity or to create the managed identity for you.Find the Service Principal ID of the managed identity:
root@rok-tools:~# export PRINCIPAL_ID=$(az identity show \ > --name ${AZ_MANAGED_IDENTITY?} \ > --resource-group ${AZ_RESOURCE_GROUP?} \ > --output tsv \ > --query principalId)Troubleshooting
The command failed with an authorization error
If the above command fails with an error message similar to the following:
ERROR: The client '0c799e27-a84f-41a2-a02b-236af002af99' with object id '0c799e27-a84f-41a2-a02b-236af002af99' does not have authorization to perform action 'Microsoft.ManagedIdentity/userAssignedIdentities/read' over scope '/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.ManagedIdentity/userAssignedIdentities/rok-arrikto-cluster' or the scope is invalid. If access was recently granted, please refresh your credentials.it means that your identity does not have sufficient permissions to retrieve a managed identity.
To proceed, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has either
OwnerorReaderpermissions. If you do not have the required permissions, contact your administrator to grant them to your identity.Find the ID of the storage account resource:
root@rok-tools:~# export STORAGE_ACCOUNT_ID=$(az storage account show \ > --resource-group ${AZ_RESOURCE_GROUP?} \ > --name ${STORAGE_ACCOUNT_NAME?} \ > --output tsv \ > --query id)Troubleshooting
The command failed with an authorization error
If the above command fails with an error message similar to the following:
(AuthorizationFailed) The client '0c799e27-a84f-41a2-a02b-236af002af99' with object id '0c799e27-a84f-41a2-a02b-236af002af99' does not have authorization to perform action 'Microsoft.Storage/storageAccounts/read' over scope '/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.Storage/storageAccounts/roka8eb022arriktoarrikto' or the scope is invalid. If access was recently granted, please refresh your credentials.it means that your identity does not have sufficient permissions to retrieve a storage account.
To proceed, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has either
OwnerorReaderpermissions. If you do not have the required permissions, contact your administrator to grant them to your identity.Assign the Storage Blob Data Contributor role to the Service Principal of the managed identity at the storage account resource scope:
root@rok-tools:~# az role assignment create \ > --role "Storage Blob Data Contributor" \ > --assignee-object-id ${PRINCIPAL_ID?} \ > --assignee-principal-type ServicePrincipal \ > --scope ${STORAGE_ACCOUNT_ID?} { "canDelegate": null, "condition": null, "conditionVersion": null, "description": null, "id": "/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.Storage/storageAccounts/roka8eb022arriktoarrikto/providers/Microsoft.Authorization/roleAssignments/60fbe008-8c02-417b-bf5a-4227b940d131", "name": "60fbe008-8c02-417b-bf5a-4227b940d131", "principalId": "87959b52-1687-4a8f-858a-2dcbeda4c22a", "principalType": "ServicePrincipal", "resourceGroup": "arrikto", "roleDefinitionId": "/subscriptions/3b63afce-113a-4798-a303-f37dada04319/providers/Microsoft.Authorization/roleDefinitions/ba92f5b4-2d11-453d-a403-e96b0029c9fe", "scope": "/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.Storage/storageAccounts/roka8eb022arriktoarrikto", "type": "Microsoft.Authorization/roleAssignments" }Troubleshooting
The command failed with an authorization error
If the above command fails with an error message similar to the following:
The client '0c799e27-a84f-41a2-a02b-236af002af99' with object id '0c799e27-a84f-41a2-a02b-236af002af99' does not have authorization to perform action 'Microsoft.Authorization/roleAssignments/write' over scope '/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.Storage/storageAccounts/roka8eb022arriktoarrikto/providers/Microsoft.Authorization/roleAssignments/2af693c3-0097-480c-8d9f-ca6dfd88f3b8' or the scope is invalid. If access was recently granted, please refresh your credentials.it means that your identity does not have sufficient permissions to create a role assignment.
To proceed, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has
Ownerpermissions. If you only haveReaderpermissions, contact your administrator to grantOwnerpermissions to your identity or to create the role assignment for you.
Verify¶
Choose one of the following options, based on how you are managing your Azure resources.
Go to the Managed Identities service in Azure Portal. Verify the managed identity you created earlier is in the list.
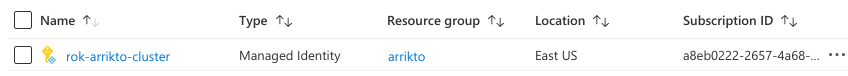
Click on the managed identity.
Click on Azure role assignments. Verify you see an assignment with the Storage Blob Data Contributor role, and the storage account you created for Rok under the Resource Name.
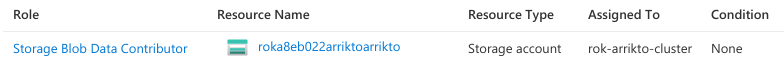
Ensure the managed identity exists:
root@rok-tools:~# az identity show \ > --name ${AZ_MANAGED_IDENTITY?} \ > --resource-group ${AZ_RESOURCE_GROUP?} { "clientId": "8801729b-2217-446f-8542-829e49bf90e9", "clientSecretUrl": "https://control-eastus.identity.azure.net/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourcegroups/arrikto/providers/Microsoft.ManagedIdentity/userAssignedIdentities/rok-arrikto-cluster/credentials?tid=2bf793e0-71b3-4a6c-ba8a-96a6755de088&oid=87959b52-1687-4a8f-858a-2dcbeda4c22a&aid=8801729b-2217-446f-8542-829e49bf90e9", "id": "/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourcegroups/arrikto/providers/Microsoft.ManagedIdentity/userAssignedIdentities/rok-arrikto-cluster", "location": "eastus", "name": "rok-arrikto-cluster", "principalId": "87959b52-1687-4a8f-858a-2dcbeda4c22a", "resourceGroup": "arrikto", "tags": {}, "tenantId": "2bf793e0-71b3-4a6c-ba8a-96a6755de088", "type": "Microsoft.ManagedIdentity/userAssignedIdentities" }Troubleshooting
The command failed with an authorization error
If the above command fails with an error message similar to the following:
ERROR: The client '0c799e27-a84f-41a2-a02b-236af002af99' with object id '0c799e27-a84f-41a2-a02b-236af002af99' does not have authorization to perform action 'Microsoft.ManagedIdentity/userAssignedIdentities/read' over scope '/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.ManagedIdentity/userAssignedIdentities/rok-arrikto-cluster' or the scope is invalid. If access was recently granted, please refresh your credentials.it means that your identity does not have sufficient permissions to retrieve a managed identity.
To proceed, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has either
OwnerorReaderpermissions. If you do not have the required permissions, contact your administrator to grant them to your identity.Find the Service Principal ID of the managed identity:
root@rok-tools:~# export PRINCIPAL_ID=$(az identity show \ > --name ${AZ_MANAGED_IDENTITY?} \ > --resource-group ${AZ_RESOURCE_GROUP?} \ > --output tsv \ > --query principalId)Troubleshooting
The command failed with an authorization error
If the above command fails with an error message similar to the following:
ERROR: The client '0c799e27-a84f-41a2-a02b-236af002af99' with object id '0c799e27-a84f-41a2-a02b-236af002af99' does not have authorization to perform action 'Microsoft.ManagedIdentity/userAssignedIdentities/read' over scope '/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.ManagedIdentity/userAssignedIdentities/rok-arrikto-cluster' or the scope is invalid. If access was recently granted, please refresh your credentials.it means that your identity does not have sufficient permissions to retrieve a managed identity.
To proceed, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has either
OwnerorReaderpermissions. If you do not have the required permissions, contact your administrator to grant them to your identity.Output the ID of the storage account:
root@rok-tools:~# echo ${STORAGE_ACCOUNT_ID?} /subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.Storage/storageAccounts/roka8eb022arriktoarrikto"List the roles assigned to this identity:
root@rok-tools:~# az role assignment list \ > --all \ > --assignee ${PRINCIPAL_ID?} [ { "canDelegate": null, "condition": null, "conditionVersion": null, "description": null, "id": "/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.Storage/storageAccounts/rok3b63afcarriktoarrikto/providers/Microsoft.Authorization/roleAssignments/60fbe008-8c02-417b-bf5a-4227b940d131", "name": "60fbe008-8c02-417b-bf5a-4227b940d131", "principalId": "87959b52-1687-4a8f-858a-2dcbeda4c22a", "principalName": "8801729b-2217-446f-8542-829e49bf90e9", "principalType": "ServicePrincipal", "resourceGroup": "arrikto", "roleDefinitionId": "/subscriptions/3b63afce-113a-4798-a303-f37dada04319/providers/Microsoft.Authorization/roleDefinitions/ba92f5b4-2d11-453d-a403-e96b0029c9fe", "roleDefinitionName": "Storage Blob Data Contributor", "scope": "/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.Storage/storageAccounts/roka8eb022arriktoarrikto", "type": "Microsoft.Authorization/roleAssignments" } ]Troubleshooting
The command failed with an authorization error
If the above command fails with an error message similar to the following:
The client '0c799e27-a84f-41a2-a02b-236af002af99' with object id '0c799e27-a84f-41a2-a02b-236af002af99' does not have authorization to perform action 'Microsoft.Authorization/roleAssignments/read' over scope '/subscriptions/3b63afce-113a-4798-a303-f37dada04319' or the scope is invalid. If access was recently granted, please refresh your credentials.it means that your identity does not have sufficient permissions to list role assignments.
To proceed, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has either
OwnerorReaderpermissions. If you do not have the required permissions, contact your administrator to grant them to your identity.Verify there is at least one assignment whose role is equal to Storage Blob Data Contributor and whose scope is equal to the ID of the storage account.
Summary¶
You have successfully created the cloud identity Rok will use to gain access to your platform’s object storage service.
What’s Next¶
The next step is to authorize Rok to access the object storage service using the cloud identity you created.
