Create Storage Account (Azure only)¶
This section will guide you through creating an Azure Storage Account for Rok to store its snapshot data. If you already have an Azure Storage Account, you may proceed to the Verify section.
Overview
What You’ll Need¶
- (Optional) Access to the Azure portal.
- A configured management environment.
- An existing AKS cluster.
- Permissions to create an Azure Storage Account.
Procedure¶
Switch to your management environment and define the following alias to sanitize components of the storage account name Rok will use:
root@rok-tools:~# alias sanitize="tr -cd '[:alnum:]' | tr '[:upper:]' '[:lower:]'"Sanitize the subscription ID:
root@rok-tools:~# export STORAGE_ACCOUNT_SID=$(echo ${SUBSCRIPTION_ID?} | sanitize)Sanitize the resource group:
root@rok-tools:~# export STORAGE_ACCOUNT_RGRP=$(echo ${AZ_RESOURCE_GROUP?} | sanitize)Sanitize the AKS cluster name:
root@rok-tools:~# export STORAGE_ACCOUNT_CLUSTER=$(echo ${AKS_CLUSTER?} | sanitize)Create the name of the storage account your Rok cluster will use:
root@rok-tools:~# export STORAGE_ACCOUNT_NAME="rok${STORAGE_ACCOUNT_SID:0:7}${STORAGE_ACCOUNT_RGRP:0:7}${STORAGE_ACCOUNT_CLUSTER:0:7}"Create the storage account. Choose one of the following options, based on how you are managing your Azure resources.
Obtain the name of the storage account and copy it to your clipboard, as you are going to use this value in later steps:
root@rok-tools:~# echo ${STORAGE_ACCOUNT_NAME?} roka8eb022arriktoarriktoGo to the Storage Accounts service in Azure Portal.
Click Create.
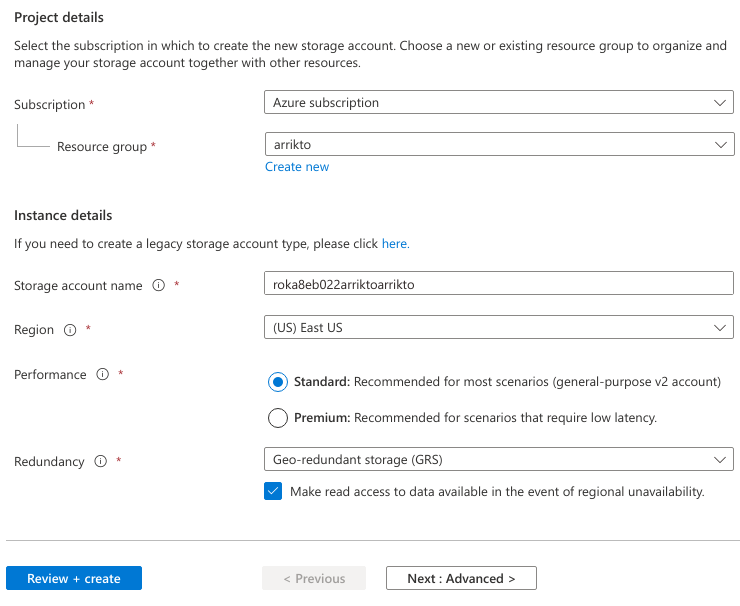
On the Basics page, set the following options:
- Set Subscription to your desired subscription.
- Set Resource Group to arrikto, so it matches the resource group of your AKS cluster.
- Set Storage account name to the storage account name you created earlier.
- Set Region to East US, so it matches the region of your AKS cluster.
- Set Performance to Standard (general-purpose v2).
Troubleshooting
The storage account name already exists
It is possible that a storage account already exists with the same name. In this case, the Azure portal UI displays the following error:

If you see this error, proceed to the Verify section to determine if you can use this storage account for your Rok installation.
Go to the Tags tab and do the following:
Obtain the subscription ID and copy it to your clipboard:
root@rok-tools:~# echo ${SUBSCRIPTION_ID?} a8eb0222-2657-4a68-ae60-f06536139029Create a new tag with Name subscription_id and paste the subscription ID from your clipboard as its Value.
Obtain the resource group and copy it to your clipboard:
root@rok-tools:~# echo ${AZ_RESOURCE_GROUP?} arriktoCreate a new tag with Name resource_group and paste the resource group from your clipboard as its Value.
Obtain the AKS cluster name and copy it to your clipboard:
root@rok-tools:~# echo ${AKS_CLUSTER?} arrikto-clusterCreate a new tag with Name aks_cluster_name and paste the AKS cluster name from your clipboard as its Value.
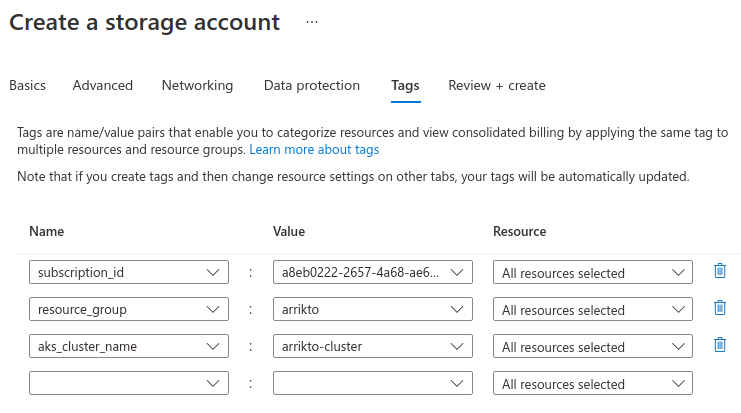
Click Review + create to use the defaults in all remaining options.
Click Create.
Ensure that the storage account does not already exist by verifying that the
nameAvailablefield of the output of the following command is equal to true:root@rok-tools:~# az storage account check-name --name ${STORAGE_ACCOUNT_NAME?} { "message": null, "nameAvailable": true, "reason": null }Troubleshooting
The storage account already exists
If the
nameAvailablefield in the above output is equal to false, then a storage account with that name already exists. In this case, proceed to the Verify section to determine if you can use this storage account for your Rok installation.The command failed with an authorization error
If the above command fails with an error message similar to the following:
(AuthorizationFailed) The client '0c799e27-a84f-41a2-a02b-236af002af99' with object id '0c799e27-a84f-41a2-a02b-236af002af99' does not have authorization to perform action 'Microsoft.Storage/checkNameAvailability/read' over scope '/subscriptions/3b63afce-113a-4798-a303-f37dada04319' or the scope is invalid. If access was recently granted, please refresh your credentials.it means that your identity does not have sufficient permissions to check the availability of a storage account name.
To proceed, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has either
OwnerorReaderpermissions. If you do not have the required permissions, contact your administrator to grant them to your identity.Create the storage account:
root@rok-tools:~# az storage account create \ > --resource-group ${AZ_RESOURCE_GROUP?} \ > --name ${STORAGE_ACCOUNT_NAME?} \ > --location ${AZURE_DEFAULTS_LOCATION?} \ > --kind StorageV2 \ > --tags subscription_id=${SUBSCRIPTION_ID?} \ > resource_group=${AZ_RESOURCE_GROUP?} \ > aks_cluster_name=${AKS_CLUSTER?} { "accessTier": "Hot", ... "id": "/subscriptions/a8eb0222-2657-4a68-ae60-f06536139029/resourceGroups/arrikto/providers/Microsoft.Storage/storageAccounts/roka8eb022arriktoarrikto", ... "kind": "StorageV2", ... "location": "eastus", ... "name": "roka8eb022arriktoarrikto", ... "primaryEndpoints": { "blob": "https://roka8eb022arriktoarrikto.blob.core.windows.net/", ... }, "primaryLocation": "eastus", ... "provisioningState": "Succeeded", "resourceGroup": "arrikto", ... "secondaryEndpoints": { "blob": "https://roka8eb022arriktoarrikto-secondary.blob.core.windows.net/", ... }, "secondaryLocation": "westus", "sku": { "name": "Standard_RAGRS", "tier": "Standard" }, "statusOfPrimary": "available", "statusOfSecondary": "available", "tags": { "aks_cluster_name": "arrikto-cluster", "resource_group": "arrikto", "subscription_id": "a8eb0222-2657-4a68-ae60-f06536139029" "type": "Microsoft.Storage/storageAccounts" }Troubleshooting
The command failed with an authorization error
If the above command fails with an error message similar to the following:
(AuthorizationFailed) The client '0c799e27-a84f-41a2-a02b-236af002af99' with object id '0c799e27-a84f-41a2-a02b-236af002af99' does not have authorization to perform action 'Microsoft.Storage/storageAccounts/write' over scope '/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.Storage/storageAccounts/roka8eb022arriktoarrikto' or the scope is invalid. If access was recently granted, please refresh your credentials.it means that your identity does not have sufficient permissions to create a storage account.
To proceed, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has
Ownerpermissions. If you only haveReaderpermissions, contact your administrator to grantOwnerpermissions to your identity or to create the storage account for you.
Verify¶
Choose one of the following options, based on how you are managing your Azure resources.
Go to the Storage Accounts service in Azure Portal.
Verify that the storage account you created earlier is in the list, its Kind is StorageV2, and belongs to the expected resource group, location and subscription.
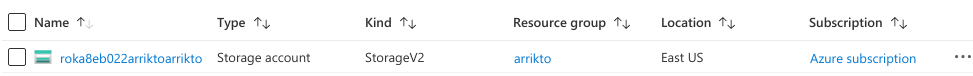
Select your storage account from the list.
Verify that the storage account has correct tags:
Select Tags from the resource menu (left sidebar).
Ensure that a subscription_id tag exists and has the following value:
root@rok-tools:~# echo ${SUBSCRIPTION_ID?} a8eb0222-2657-4a68-ae60-f06536139029Ensure that a resource_group tag exists and has the following value:
root@rok-tools:~# echo ${AZ_RESOURCE_GROUP?} arriktoEnsure that an aks_cluster_name tag exists and has the following value:
root@rok-tools:~# echo ${AKS_CLUSTER?} arrikto-cluster
Troubleshooting
The storage account tags are missing
If the storage account exists but its tags are missing then it either does not belong to a Rok cluster, or it belongs to a Rok cluster of version 1.3 or earlier. Go back to step 5 of the Procedure and select a new, unique name for the storage account by setting the STORAGE_ACCOUNT_NAME environment variable, and then use it in the Storage account name field.
The storage account tags do not match
If the storage account tags exist but do not match the expected values for your cluster, then this storage account belongs to a different Rok installation. Go back to step 5 of the Procedure and select a new, unique name for the storage account by setting the STORAGE_ACCOUNT_NAME environment variable, and then use it in the Storage account name field.
Verify that the storage account has no containers:
- Select Containers from the resource menu (left sidebar).
- Ensure that there are no containers in this storage account.
Troubleshooting
Containers exist in the storage account
If the storage account tags match but containers exist, then the storage account belongs to a previous installation of Rok in the same cluster. In this case, make sure you have followed the instructions in the Clean Up section to remove all resources belonging to your previous installation of Rok.
Display the storage account:
root@rok-tools:~# az storage account show \ > --resource-group ${AZ_RESOURCE_GROUP?} \ > --name ${STORAGE_ACCOUNT_NAME?} \ > -o table AccessTier CreationTime EnableHttpsTrafficOnly Kind Location Name PrimaryLocation ProvisioningState ResourceGroup SecondaryLocation StatusOfPrimary StatusOfSecondary ------------ -------------------------------- ------------------------ --------- ---------- ------------------------ ----------------- ------------------- --------------- ------------------- ----------------- ------------------- Hot 2021-07-13T14:15:03.525036+00:00 True StorageV2 eastus roka8eb022arriktoarrikto eastus Succeeded arrikto westus available availableTroubleshooting
The command failed with an authorization error
If the above command fails with an error message similar to the following:
(AuthorizationFailed) The client '0c799e27-a84f-41a2-a02b-236af002af99' with object id '0c799e27-a84f-41a2-a02b-236af002af99' does not have authorization to perform action 'Microsoft.Storage/storageAccounts/read' over scope '/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.Storage/storageAccounts/roka8eb022arriktoarrikto' or the scope is invalid. If access was recently granted, please refresh your credentials.it means that your identity does not have sufficient permissions to retrieve a storage account.
To proceed, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has either
OwnerorReaderpermissions. If you do not have the required permissions, contact your administrator to grant them to your identity.Verify that the storage account you created earlier is in the above table, its Kind is StorageV2, and belongs to the expected resource group, location and subscription.
Verify that the storage account has correct tags:
Retrieve the subscription_id tag of the storage account:
root@rok-tools:~# az storage account show \ > --resource-group ${AZ_RESOURCE_GROUP?} \ > --name ${STORAGE_ACCOUNT_NAME?} \ > --query tags.subscription_id \ > --output tsv a8eb0222-2657-4a68-ae60-f06536139029Troubleshooting
The command failed with an authorization error
If the above command fails with an error message similar to the following:
(AuthorizationFailed) The client '0c799e27-a84f-41a2-a02b-236af002af99' with object id '0c799e27-a84f-41a2-a02b-236af002af99' does not have authorization to perform action 'Microsoft.Storage/storageAccounts/read' over scope '/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.Storage/storageAccounts/roka8eb022arriktoarrikto' or the scope is invalid. If access was recently granted, please refresh your credentials.it means that your identity does not have sufficient permissions to retrieve a storage account.
To proceed, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has either
OwnerorReaderpermissions. If you do not have the required permissions, contact your administrator to grant them to your identity.Display your desired subscription:
root@rok-tools:~# echo ${SUBSCRIPTION_ID?} a8eb0222-2657-4a68-ae60-f06536139029Ensure that the two values above match.
Retrieve the resource_group tag of the storage account:
root@rok-tools:~# az storage account show \ > --resource-group ${AZ_RESOURCE_GROUP?} \ > --name ${STORAGE_ACCOUNT_NAME?} \ > --query tags.resource_group \ > --output tsv arriktoTroubleshooting
The command failed with an authorization error
If the above command fails with an error message similar to the following:
(AuthorizationFailed) The client '0c799e27-a84f-41a2-a02b-236af002af99' with object id '0c799e27-a84f-41a2-a02b-236af002af99' does not have authorization to perform action 'Microsoft.Storage/storageAccounts/read' over scope '/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.Storage/storageAccounts/roka8eb022arriktoarrikto' or the scope is invalid. If access was recently granted, please refresh your credentials.it means that your identity does not have sufficient permissions to retrieve a storage account.
To proceed, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has either
OwnerorReaderpermissions. If you do not have the required permissions, contact your administrator to grant them to your identity.Display your resource group:
root@rok-tools:~# echo ${AZ_RESOURCE_GROUP?} arriktoEnsure that the two values above match.
Retrieve the aks_cluster_name tag of the storage account:
root@rok-tools:~# az storage account show \ > --resource-group ${AZ_RESOURCE_GROUP?} \ > --name ${STORAGE_ACCOUNT_NAME?} \ > --query tags.aks_cluster_name \ > --output tsv arrikto-clusterTroubleshooting
The command failed with an authorization error
If the above command fails with an error message similar to the following:
(AuthorizationFailed) The client '0c799e27-a84f-41a2-a02b-236af002af99' with object id '0c799e27-a84f-41a2-a02b-236af002af99' does not have authorization to perform action 'Microsoft.Storage/storageAccounts/read' over scope '/subscriptions/3b63afce-113a-4798-a303-f37dada04319/resourceGroups/arrikto/providers/Microsoft.Storage/storageAccounts/roka8eb022arriktoarrikto' or the scope is invalid. If access was recently granted, please refresh your credentials.it means that your identity does not have sufficient permissions to retrieve a storage account.
To proceed, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has either
OwnerorReaderpermissions. If you do not have the required permissions, contact your administrator to grant them to your identity.Display the name of your AKS cluster:
root@rok-tools:~# echo ${AKS_CLUSTER?} arrikto-clusterEnsure that the two values above match.
Troubleshooting
The storage account tags are missing
If the storage account exists but its tags are missing then it either does not belong to a Rok cluster, or it belongs to a Rok cluster of version 1.3 or earlier. Go back to step 5 of the Procedure and select a new, unique name for the storage account by setting the STORAGE_ACCOUNT_NAME environment variable, and then proceed to create a new storage account with that name.
The storage account tags do not match
If the storage account tags exist but do not match the expected values for your cluster, then this storage account belongs to a different Rok installation. Go back to step 5 of the Procedure and select a new, unique name for the storage account by setting the STORAGE_ACCOUNT_NAME environment variable, and then proceed to create a new storage account with that name.
Verify that the storage account has no containers:
root@rok-tools:~# az storage container list \ > --account-name ${STORAGE_ACCOUNT_NAME?} \ > --auth-mode login []Troubleshooting
Containers exist in the storage account
If the storage account tags match but containers exist, then the storage account belongs to a previous installation of Rok in the same cluster. In this case, make sure you have followed the instructions in the Clean Up section to remove all resources belonging to your previous installation of Rok.
The command failed with an authorization error
If the above command fails with an error similar to the following:
You do not have the required permissions needed to perform this operation. Depending on your operation, you may need to be assigned one of the following roles: "Storage Blob Data Contributor" "Storage Blob Data Reader" "Storage Queue Data Contributor" "Storage Queue Data Reader" If you want to use the old authentication method and allow querying for the right account key, please use the "--auth-mode" parameter and "key" value.it means that your CLI does not have permissions to list the containers of a storage account.
In this case, make sure you have followed the Configure Azure CLI section to configure your Azure CLI with an identity that has either
OwnerorReaderpermissions. If you do not have the required permissions, contact your administrator to grant them to your identity.
What’s Next¶
The next step is to create an Azure Managed Identity and provide it with permissions on your storage account so Rok can use it to access Azure Blob Storage.
