Configure Access to Arrikto’s Private Registry¶
Arrikto distributes container images via a private Container Registry on Google Cloud (gcr.io). This guide will walk you through configuring access to this private registry.
Fast Forward
If you have already decrypted the Arrikto-provided Docker configuration file, expand this box to fast-forward.
Go to your GitOps repository, inside your
rok-toolsmanagement environment:root@rok-tools:~# cd ~/ops/deploymentsRun:
root@rok-tools:~/ops/deployments# cat > deploy/dockerconfig.jsonCaution
This will save your Docker configuration file unencrypted in
~/ops/deployments/deploy/dockerconfig.json.Note
The above command will appear to hang while it is waiting for the decrypted text. Proceed to the next step to give the necessary input.
Copy the decrypted text.
Paste the decrypted text into the terminal.
Press
Enterand thenCtrl+Dto informcatthat there is no more input.Save your state:
root@rok-tools:~/ops/deployments# rok-j2 deploy/env.arriktoreg.j2 -o deploy/env.arriktoregCommit your changes:
root@rok-tools:~/ops/deployments# git commit \ > -am "Configure Access to Arrikto's Private Registry"Proceed to the Verify section.
Choose one of the following options to configure access to Arrikto’s private registry:
- Option 1: Configure Access to Arrikto’s Private Registry Automatically (preferred).
- Option 2: Configure Access to Arrikto’s Private Registry Manually.
Air Gapped
Arrikto uses a private registry hosted at gcr.io to share images for Rok
and Arrikto Enterprise Kubeflow. Follow the rest of this guide and configure
Docker credentials. You will need them to mirror images from the Arrikto
private registry to your private registry, later on.
Overview
What You’ll Need¶
Your clone of the Arrikto GitOps repository.
The encrypted Docker JSON configuration file, which is similar to the following:
dockerconfig_dummy.asc1 -----BEGIN PGP MESSAGE----- 2 3 jA0ECQMCZYE2c+tkxZf00ocBYakv/K62OUtCVQz/P8Xq9j6FQK+2y/AsNFQZdnqT 4-5 4 bOnutQa3iSeCjH9SPnaHWLAoyyULGxA8DWpnrjK6a0lkHyM8shyJufOL5kCgHHmq 5 ZZ9R5O8+6UgEPfzZZ8r2A8UcOpOY07L+K/K0eI0oRn0ShTPffVvfR+a5U6WqapF/ 6 3eeSgHnfY0w= 7 =6Ssd 8 -----END PGP MESSAGE----- The passphrase to decrypt the above.
Contact Arrikto
If you don’t have any of the above items, please contact the Arrikto Tech Team to provide them to you.
Option 1: Configure Access to Arrikto’s Private Registry Automatically (preferred)¶
Configure access to Arrikto’s private registry by following the on-screen
instructions on the rok-deploy user interface.
If rok-deploy is not already running, start it with:
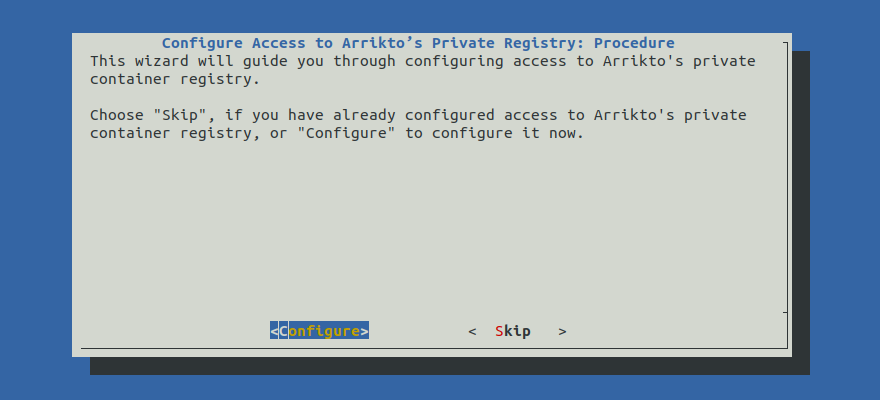
Proceed to the Summary section.
Option 2: Configure Access to Arrikto’s Private Registry Manually¶
If you want to configure access to Arrikto’s private registry manually, follow this section.
Procedure¶
Go to your GitOps repository, inside your
rok-toolsmanagement environment:root@rok-tools:~# cd ~/ops/deploymentsDecrypt the Docker configuration file:
root@rok-tools:~/ops/deployments# gpg -d > deploy/dockerconfig.jsonCaution
This will save your Docker configuration file unencrypted in
~/ops/deployments/deploy/dockerconfig.json.Note
The above command will appear to hang while it is waiting for the encrypted text. Proceed to the next step to give the necessary input.
Copy the encrypted text from the email, including the
-----BEGIN PGP MESSAGE-----and-----END PGP MESSAGE-----lines.Paste the encrypted text into the terminal, including the
-----BEGIN PGP MESSAGE-----and-----END PGP MESSAGE-----lines.Enter the passphrase when
gpgprompts you to.Press
Ctrl+Dto informgpgthat there is no more input.Save your state:
root@rok-tools:~/ops/deployments# rok-j2 deploy/env.arriktoreg.j2 -o deploy/env.arriktoregCommit your changes:
root@rok-tools:~/ops/deployments# git commit \ > -am "Configure Access to Arrikto's Private Registry"
Verify¶
Go to your GitOps repository, inside your
rok-toolsmanagement environment:root@rok-tools:~# cd ~/ops/deploymentsSet the GCR project and image tag which you will use to verify access to Arrikto’s private container registry:
root@rok-tools:~/ops/deployments# export GCR_PROJECT=arrikto-deployroot@rok-tools:~/ops/deployments# export GCR_IMAGE_TAG=release-2.0-l0-release-2.0.2Get the authentication token from your
dockerconfig.jsonfile:root@rok-tools:~/ops/deployments# export TOKEN=$(cat deploy/dockerconfig.json \ > | jq -r '.auths ."gcr.io" .auth')Exchange the above token with a bearer token for the GCR project:
root@rok-tools:~/ops/deployments# export REGISTRY_TOKEN=$(curl -s \ > --header "Authorization: Basic ${TOKEN?}" \ > "https://gcr.io/v2/token?service=gcr.io&scope=registry:${GCR_PROJECT?}/roke:pull" \ > | jq -r '.token')Access the image container registry by pulling the manifests of the image you specified at step 2:
root@rok-tools:~/ops/deployments# curl -s \ > --header "Authorization: Bearer ${REGISTRY_TOKEN?}" \ > "https://gcr.io/v2/${GCR_PROJECT?}/roke/manifests/${GCR_IMAGE_TAG?}" \ > | jq -e '.config .digest' > /dev/null && echo OK OK
What’s Next¶
The next step is to create a VPC for your Kubernetes cluster.
