PingID¶
This section will guide you through using PingID as an OIDC provider for Kubeflow.
See also
Overview
What You’ll Need¶
- A configured management environment.
- Your clone of the Arrikto GitOps repository.
- An existing Kubernetes cluster.
- A working Rok deployment.
- A working Kubeflow deployment.
- Access to the cluster running services.
- Access to the PingOne admin console.
Procedure¶
From the home of your admin console go to Add Environment (in the top right corner of the page) -> Customer solution -> Next -> Next and create a new environment:
Environment¶ Environment Name <ENVIRONMENT>Replace
<ENVIRONMENT>with the name of your environment, for exampleKubeflow.Select your environment from the home page of your admin console.
From your admin console go to Connections (it’s an icon in the left sidebar) -> Applications -> Add Application -> Web App -> OIDC, and create an application with the following settings:
Application¶ Application Name <APPLICATION_NAME>Authorized redirect URIs <FQDN>/authservice/oidc/callbackScopes profile(Allows read-only access to the user’s personal information using OpenID Connect)email(Allows read-only access to the user’s primary email address using OpenID Connect)
User ID subRefresh Token Enable the Refresh Token generation. Replace:
<APPLICATION_NAME>with the name of your application, for exampleKubeflow.<FQDN>with the public URL of your EKF installation, for examplehttps://arrikto-cluster.apps.example.com.
Important
Ensure that you have enabled the Refresh Token generation for your PingOne application. PingOne applications do not generate Refresh Tokens with the default configurations.
Enable Refresh Token generation
Log in to the PingOne admin console.
Click on your application environment.
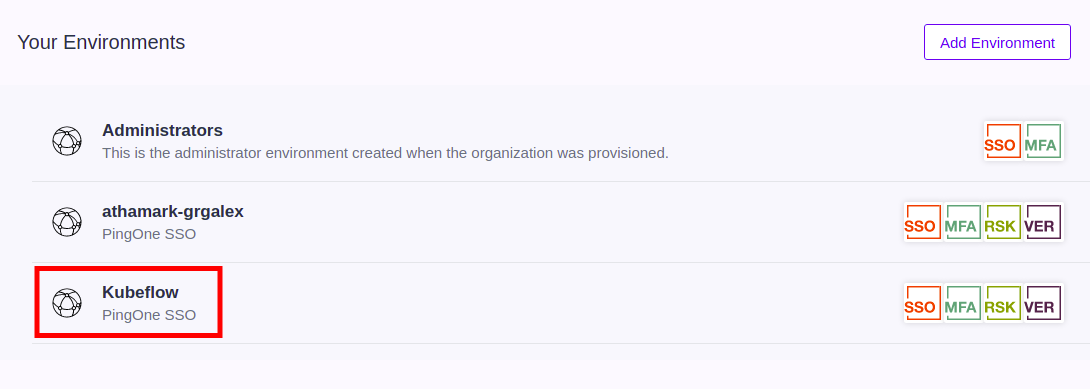
Click on the Connections tab on the left side menu and then select the Applications tab.
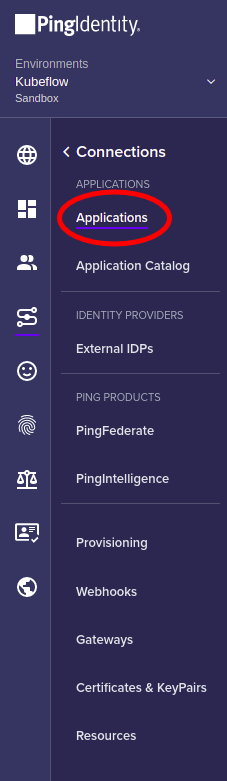
Click on your PingOne application.
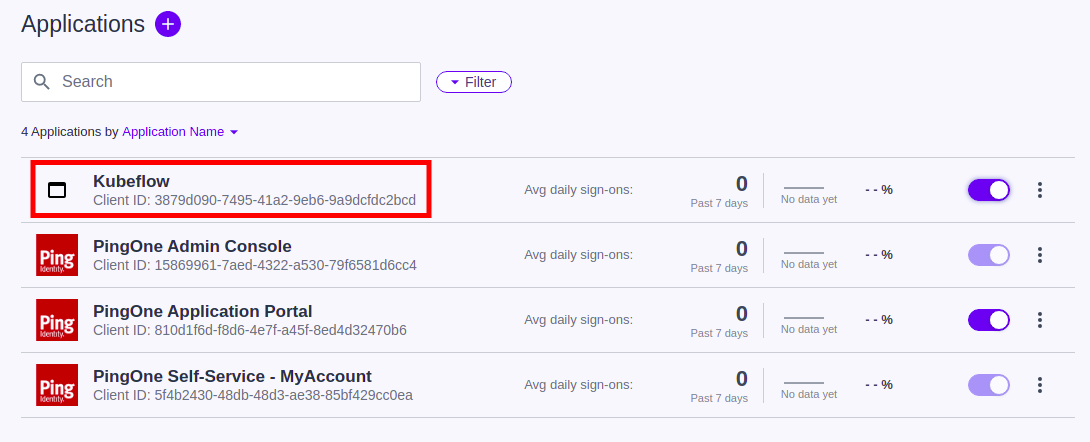
Click on the Configuration tab.
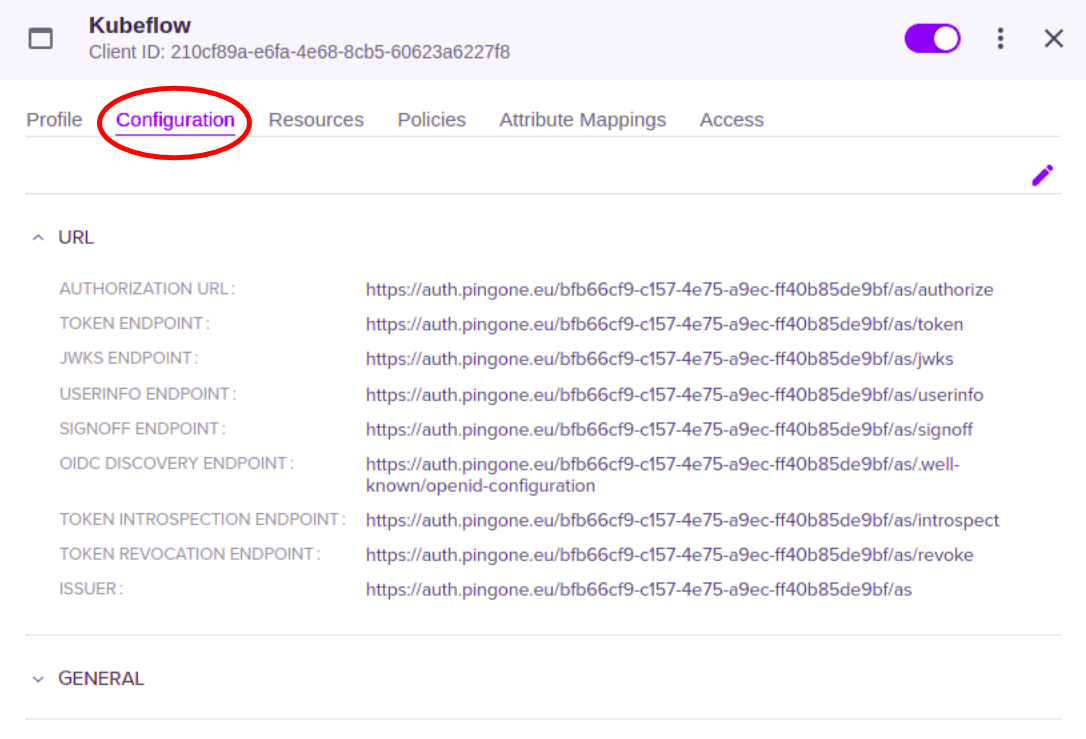
Click on the pencil icon to modify the configurations of your application.
Expand the GENERAL dropdown menu.
Check the Refresh Token option.
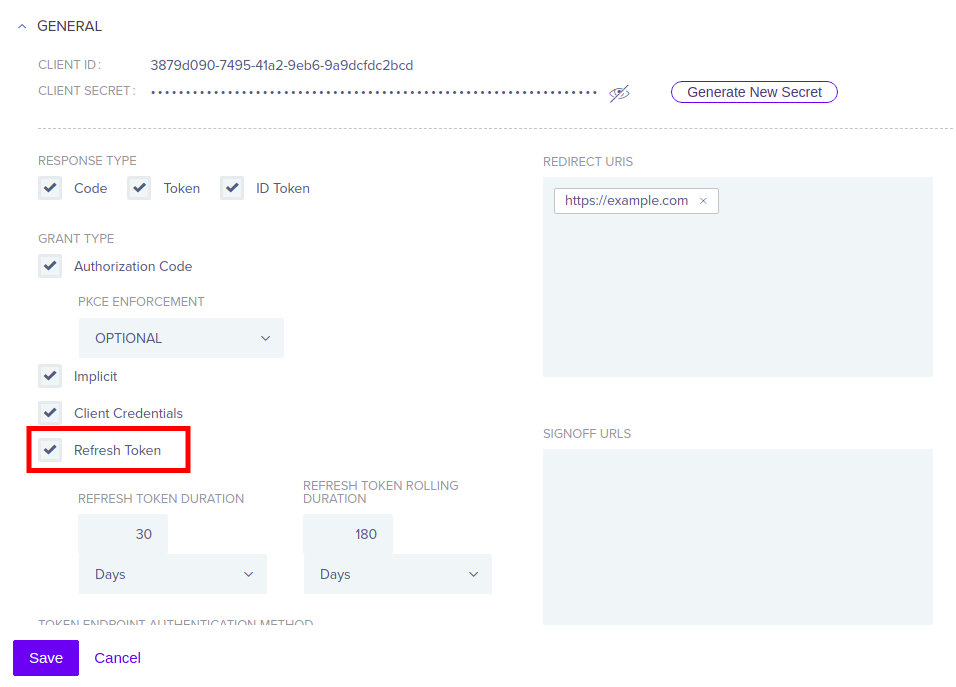
Click on the Save button.
From your admin console go to Connections -> Applications, then find your application and click on the slide button to activate it and enable user access to it.
Expand the application info using the drop-down button at the right side of the application window, if it’s not expanded already.
Click on the Configuration tab and copy the following info, which will be used in the next steps:
ISSUERCLIENT IDCLIENT SECRET
Go to your GitOps repository, inside your
rok-toolsmanagement environment:root@rok-tools:/# cd ~/ops/deploymentsSpecify the client ID:
root@rok-tools:~/ops/deployments# export OIDC_CLIENT_ID=<CLIENT ID>Replace
<CLIENT ID>with the client ID you copied from the Configuration tab.Specify the client secret:
root@rok-tools:~/ops/deployments# export OIDC_CLIENT_SECRET=<CLIENT SECRET>Replace
<CLIENT SECRET>with the client secret you copied from the Configuration tab.Render the AuthService credentials:
root@rok-tools:~/ops/deployments# j2 kubeflow/manifests/common/oidc-authservice/overlays/deploy/secret_params.env.j2 \ > -o kubeflow/manifests/common/oidc-authservice/overlays/deploy/secret_params.envSet the public URL of your EKF installation:
root@rok-tools:~/ops/deployments# export FQDN=<FQDN>Replace
<FQDN>with your installation’s public URL. For example:root@rok-tools:~/ops/deployments# export FQDN=https://arrikto-cluster.apps.example.comSet the public URL of your application:
root@rok-tools:~/ops/deployments# export OIDC_PROVIDER=<ISSUER>Replace
<ISSUER>with the issuer URL you copied from the Configuration tab.Configure AuthService to convert user emails to usernames:
root@rok-tools:~/ops/deployments# export USERID_TRANSFORMERS='[{"matches": "@<DOMAIN>", "replaces": "" }]'Replace
<DOMAIN>with the domain of your organization. For example:root@rok-tools:~/ops/deployments# export USERID_TRANSFORMERS='[{"matches": "@example\\.com", "replaces": "" }]'Make sure to include
\\. With this example domain, AuthService will convert user IDs likeuser@example.comintouser.Note
USERID_TRANSFORMERSaccepts a JSON formatted list of UserID transformation rules with the following format:USERID_TRANSFORMERS=[{"matches": "regex", "replaces": "value" }]AuthService will transform the UserID by finding the first transformation rule that matches
regexand replacing it withvalue.Set the default PingID settings and render the AuthService configuration:
root@rok-tools:~/ops/deployments# export USERID_CLAIM=preferred_username root@rok-tools:~/ops/deployments# export OIDC_SCOPES=profile,email,openid root@rok-tools:~/ops/deployments# export AUTHSERVICE_URL_PREFIX=${FQDN?}/authservice/ root@rok-tools:~/ops/deployments# export TEMPLATE_PATH='' root@rok-tools:~/ops/deployments# j2 kubeflow/manifests/common/oidc-authservice/overlays/deploy/params.env.j2 \ > -o kubeflow/manifests/common/oidc-authservice/overlays/deploy/params.envSee also
Commit your changes:
root@rok-tools:~/ops/deployments# git commit -am "Use the PingID OIDC provider for Kubeflow authentication"Apply the manifests:
root@rok-tools:~/ops/deployments# rok-deploy --apply install/kubeflowRestart the pods manually:
root@rok-tools:~/ops/deployments# kubectl delete pods -n istio-system -l app=authservice
Verify¶
Ensure that the
authserviceStatefulSet is running. Verify that field STATUS is Running and field READY is 1/1:root@rok-tools:~/ops/deployments# kubectl get pods -n istio-system -l app=authservice NAME READY STATUS RESTARTS AGE authservice-0 1/1 Running 0 13sLog in with your PingID credentials at
<FQDN>, where<FQDN>is the public URL of your EKF installation. For example,https://arrikto-cluster.apps.example.com.
